Cyber-attacks are a growing threat to organizations of all sizes, and it is critical for companies to understand the various types of attacks they may face. Here are the top 10 types of cyber-attacks that can hamper an organization’s security:

Top 10 types of cyber-attacks
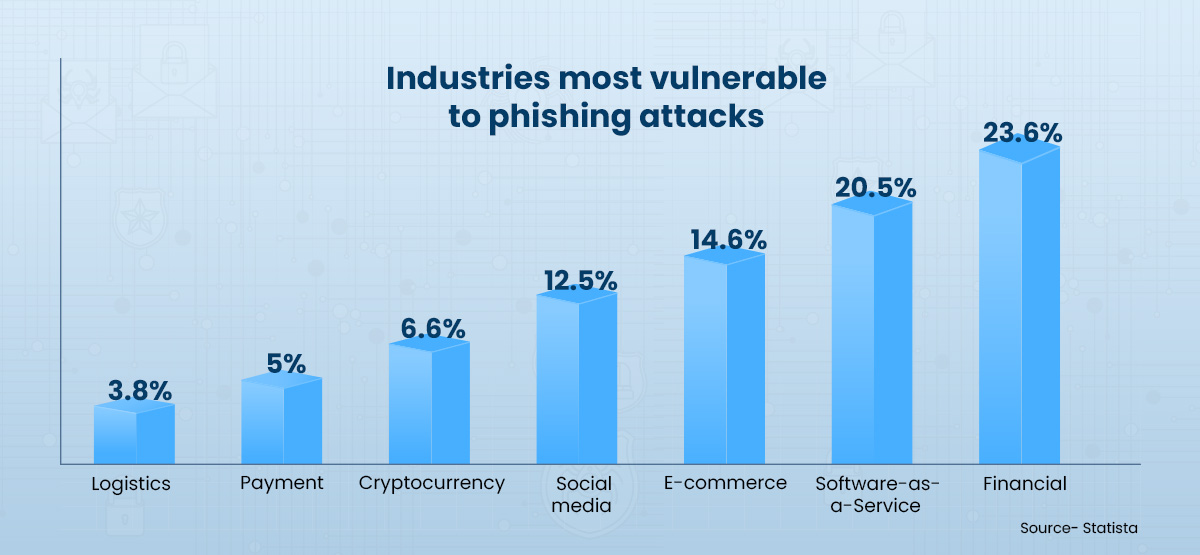
Phishing:
This type of attack is used to steal sensitive information or login credentials by tricking individuals into revealing their passwords or other personal information through fraudulent emails or websites.
Here is a list of some key cyberattack statistics as per IBM’s 2022 Cost of Data Breach Report-
- With 16% of breaches, phishing was the second most common cause, costing $4.91 million.
- During this year, 19% of data breaches used stolen or compromised credentials as their main attack vector.
- Averaging $4.5 million, breaches brought on by lost or stolen passwords.
- With a 243-day identification period and an 84-day containment period, this type of breach had the longest life cycle.
- The average amount of time taken to find and contain a data breach is 16.6% longer than this amount of time.
- With a 16% frequency and a cost of $4.91m, phishing was the second most frequent reason for breaches.
Ransomware
In a ransomware attack, hackers encrypt an organization’s data and demand a ransom payment for its release. These attacks can cripple an organization’s operations and result in significant financial losses. In 2022, ransomware remained the most common type of malware. As a result of its capacity to extort large amounts of money, it has grown in popularity among cybercriminals. Cybereason. Ransomware attacks surged dramatically in 2022, with 25% of all breaches involving ransomware attacks, according to Verizon’s 2022 Data Breach Investigations Report.
Malware
Malware attacks involve introducing malicious software into an organization’s systems to steal data or disrupt operations. Common types of malware include viruses, Trojans, and spyware. Viruses are spread more widely by employees with infected machines. 61 percent of organizations experienced malware spread by employees in 2020. By 2021, it had risen to 74 percent; by 2022, it had reached 75 percent – the highest infection rate since the SOES survey began in 2016.
Denial of Service (DoS)
DoS attacks are used to overload a network or website to make it unavailable to users. These attacks can result in significant downtime and lost revenue. Additionally, it makes it challenging for the host to recognize and defend itself against the real source of the attack. Legitimate users cannot access network resources like information systems and devices. That’s terrible news for hosts and their clients. Unfortunately, that’s also the primary security feature many of the best web hosting providers take pride in preventing DDoS attacks from disrupting services.
It is relatively easy to launch a DDoS attack and extremely difficult to mitigate it. DDoS attacks are often too massive to handle, even with some quality CDN providers. Here are some important cyberattack statistics related to DoS attacks
- In 2022, the YoY DDoS growth is 109%.
- In Q2 of 2021, the average DDoS attack lasted 30 minutes; a year later, they averaged 50 hours.

SQL Injection
In an SQL injection attack, hackers manipulate a database through user input on a website to access sensitive information. These attacks can result in the theft of sensitive data, such as financial information or intellectual property.

No comments:
Post a Comment